On October 21, one of the largest DDoS attacks ever caused massive outages on the World Wide Web for hours. Sites and services like Amazon, Spotify, Twitter, Netflix and more were largely taken offline for hours. How did this happen? Well, it starts with millions of IOT (Internet of Things) devices being unsecured and used as a pawn for a nasty botnet named Mirai.
The cyber attack began with an attack on a company called DYN. DYN provides traffic, data, DNS and analytics services to hundreds of websites and Internet companies (including SecurityCoverage). Once they recognized the DDoS attack, they were able to stop the attack in about 2 hours. After restoring service, they were attacked two more times, but were able to stop the threats fairly quickly. But, in certain areas of the country, people were not able to access a number of popular websites or services for hours.
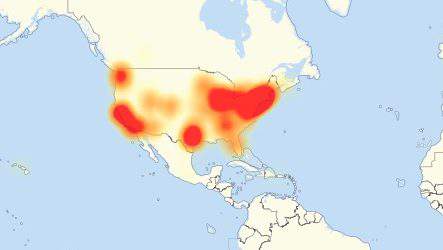
So where do the IOT devices fit in to this story? The Mirai botnet infected around 10 million IOT devices which in turn bombarded DYN’s network with traffic. This was done by Mirai “brute force” guessing the usernames and passwords for these IOT devices. Since users of these devices rarely change the default usernames and passwords, botnets like Mirai have a library of commonly used user credentials. Once the devices were taken over, the attack could begin.
Some businesses have even started recalls of their devices due to these sorts of take overs.
So what can businesses do to stop future attacks like this? Honestly, not much. There will always be people attacking cyber infrastructure. Trying to steal data or just ruin your day. But, device users don’t have to be a part of the problem. Encourage your customers to change default usernames and passwords on all of their IOT devices. Use safe, generated passwords with mixed characters, capital and lowercase letters and numbers. Of course using a robust anti-virus solution and helps and be sure to backup data. This will not be the last we see of Mirai.



