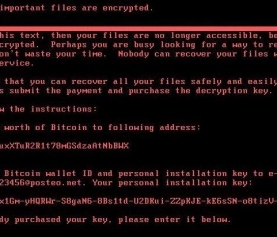
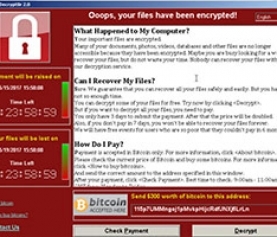
CryptoWall 3.0 is estimated to have generated $325 million in ransom from hundreds of thousands of victims worldwide this past year. As we near the peak holiday shopping season a bigg
er threat has emerged, CryptoWall 4.0. Both versions are spread primarily by spam mail, with common examples posing as copies of resumes and Fed-Ex tracking notifications. Once CryptoWall is on the system it encrypts the files and generates a message demanding ransom to decrypt the files.
CryptoWall 4.0 has been enhanced:
Encrypts file names in addition to the file in order to increase anxiety and generate more ransom payments.
The ransom notice is in HTML and now includes two sections, a notice that they have become part of the “CryptoWall Community” and a note that their intentions are not malicious but rather that they’re trying to increase security for consumers!
The attachment contains a “.js” (JavaScript) file. When that is executed, the infection downloads an executable file and saves it to C:\Windows\Temp at which point it becomes executed.
How to prevent infection or minimize impact:
- Don’t open spam emails, or emails from unrecognized senders
- Don’t open attachments from suspicious emails (for example, if you get a suspicious Fed-Ex email call them or go to their direct website instead)
- Ensure all operating system and anti-virus software are up-to-date
- Regularly back up important files and data (ex – FileHopper Plus)
- Use anti-virus and anti-malware products
How to recover files:
- If you have been backing up your system regularly you can restore from a backup
- You could pay the ransom to get a decryption key, although this does not guarantee you will get the decryption key
SecurityCoverage recommends that you make your employees and customers aware of this new ransomware threat, and remind them to be safe online.